5 minute read
Secure software development lifecycle (SSDLC): A complete guide [2023]
Secure Software Development Lifecycle is used to integrate security measures in the software development process. Explore the steps of the SSDLC process.
Table of contents
"Cybercrime is the greatest threat to every company in the world." - Ginni Rommety (Ex-CEO, IBM)
Security Software Development Life Cycle (SSDLC) is a process that integrates security considerations into every phase of the software development lifecycle.
SSDLC is designed to identify and mitigate security risks early in the development process rather than trying to fix them after the software has been deployed.
SDLC and secure SDLC
Software Development Life Cycle (SDLC) is a process that outlines the stages involved in the development of software.
It typically includes the following phases:
- Planning,
- Requirements,
- Design,
- Implementation,
- Testing,
- Deployment,
- Maintenance.
SDLC goal is to ensure that software is developed in a structured and organized manner, with a focus on creating high-quality software that meets the needs of the end-users.
Secure Software Development Life Cycle (SSDLC) is similar to the SDLC but has a focus on ensuring the security of the software. It also includes the same phases as the SDLC, but with additional steps and activities to identify and mitigate security risks throughout the development process.
SSDLC goal is to build more secure software by incorporating security into the design, development, testing, and maintenance of software.
The main difference between SDLC and SSDLC is that the first focuses on the development of software, while the second focuses on the development of secure software.
SDLC does not consider security parameters during the development process, while SSDLC integrates security into every phase of the development process.
In summary, SSDLC is an extension of SDLC and focuses on security aspects of the software development process.
Phases of SSDLC
Each step in the process has a specific purpose, and security is involved in each step.
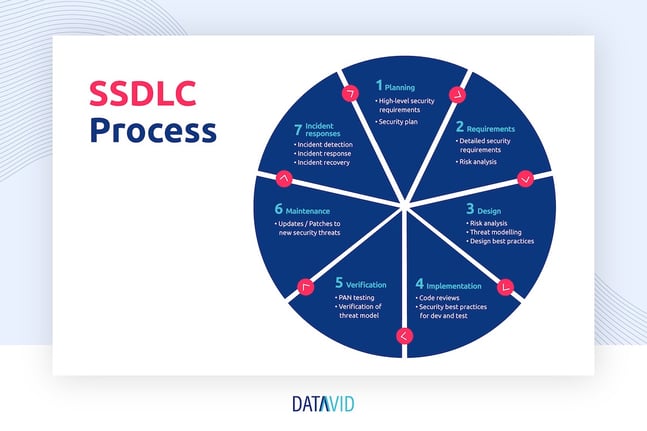
#1 Planning
In this first phase, security requirements and constraints are identified, and a security plan is developed.
This includes identifying the types of data that will be stored and processed by the software, as well as the potential threats and vulnerabilities that could be used to exploit the software.
The security plan is used to guide the development process and to ensure that security is integrated throughout the entire process.
#2 Requirements
In phase two, security requirements are included in the software requirements.
This includes identifying the required security features, such as access controls, encryption, and authentication.
The security requirements are used to guide the software's design and development and ensure that the software meets the organisation's security needs.
#3 Design
In this three, security is incorporated into the software design.
This includes using threat modelling and other design techniques to identify potential threats and vulnerabilities and to design the software to mitigate these risks.
The design should also include the use of secure coding practices, such as input validation and error handling, to ensure that the software is robust and can withstand attacks.
#4 Implementation
In phase four, the software is coded. This includes writing secure code, following best practices and guidelines for secure coding, and conducting security code reviews. The code should be written to meet the security requirements and to follow the design.
It is important to use secure coding practices to prevent common coding errors such as buffer overflow and SQL injection.
#5 Verification
In phase five, the software is tested to ensure it meets security requirements.
This includes performing security testing such as penetration testing and performing threat modelling.
Penetration testing is a method of simulating an attack on the software to identify vulnerabilities. Threat modelling is a process of identifying potential threats and vulnerabilities and determining the risk associated with each threat.
#6 Maintenance
In phase six, the software is continuously monitored and updated to address new security threats and vulnerabilities.
This includes monitoring for security alerts and patches and applying them to the software as needed.
It is important to keep the software up to date to ensure that it is protected against new security threats.
#7 Incident response
In the last phase, an incident response plan is in place to detect, respond and recover from security incidents.
This includes identifying potential incident scenarios, such as a data breach or a system compromise, and developing a plan to respond to these incidents.
The incident response plan should include procedures for incident detection, incident response, and incident recovery.
Best practices for Secure SDLC
There are best practices to follow in order to have a more efficient and functional SDLC process for your company and employees.
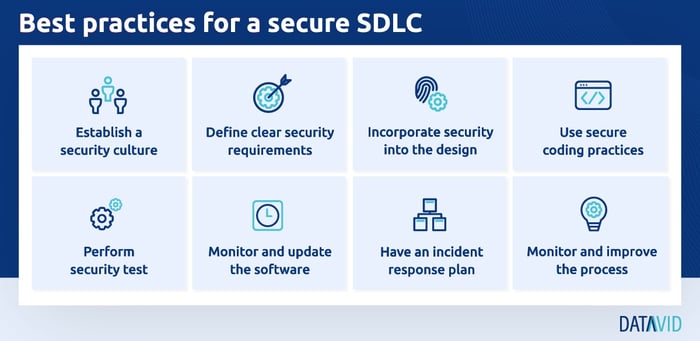
- Establish a security culture: Ensure that all employees understand the importance of security and are aware of their role in maintaining the security of the software.
- Define clear security requirements: Identify the security requirements early in the development process and ensure that they are included in the software requirements.
- Incorporate security into the design: Incorporate security into the software design by using threat modelling and other design techniques.
- Use secure coding practices: Ensure that all code is written securely, following best practices and guidelines for secure coding.
- Security test: Perform security testing to identify vulnerabilities and ensure that the software meets security requirements.
- Monitor and update the software: Continuously monitor the software for new security threats and update it as needed.
- Have an incident response plan: Have an incident response plan in place to detect, respond and recover from security incidents.
- Continuously monitor and improve the process: Continuously monitor and improve the SSDLC process to adapt to the ever-changing threat landscape.
Why do companies need a secure SDLC?
Companies need a Secure Software Development Life Cycle (SSDLC) to protect their software from security threats and to comply with industry standards and regulations.
The main reasons why companies need SSDLC are:
- Protecting sensitive data: Software is often used to store, process, and transmit sensitive data, such as personal information, financial data, and other confidential information. A SSDLC helps to ensure this data is protected against unauthorised access, theft, or leakage.
- Meeting compliance requirements: Many industries are subject to strict compliance regulations (e. g. HIPAA, PCI-DSS, and SOC2) that require companies to implement security controls to protect sensitive data. An SSDLC can help companies to meet these compliance requirements by ensuring that security is integrated into the development process.
- Reducing security risks: Software vulnerabilities can be exploited by attackers to gain unauthorised access to systems and data. An SSDLC helps to reduce the risk of security vulnerabilities by identifying and mitigating security risks early in the development process.
- Protecting the company's reputation: A data breach or security incident can cause significant damage to a company's reputation and can lead to financial losses. An SSDLC can help to prevent such incidents by ensuring that the software is developed with security in mind.
- Saving costs: Addressing security issues after the software has been deployed can be more costly and time-consuming than addressing them during the development process. An SSDLC can help to save costs by identifying and mitigating security risks early in the development process.
In summary, an SSDLC is an essential process for software development as it helps companies to protect sensitive data, meet compliance requirements, reduce security risks.
Ensure SSDLC for your business
To ensure a secure Software Development Life Cycle (SDLC), it is important to:
- Incorporate security requirements into the project requirements document
- Use a secure development methodology, such as OWASP or NIST
- Regularly train and educate all team members on security best practices
- Use threat modelling to identify and mitigate potential security risks
- Conduct regular code reviews to identify and fix vulnerabilities
- Use static and dynamic testing tools to test for vulnerabilities
- Use version control and maintain documentation
- Regularly update and patch software as needed
- Conduct penetration testing before deployment
- Have an incident response plan in place for handling security incidents.
The SSDLC process is not a one-time event but rather an ongoing process that needs to be continuously monitored and improved to adapt to the ever-changing threat landscape.
Organizations should also be prepared to respond to security incidents and have an incident response plan in place.
Frequently Asked Questions
What is SSDLC?
The SSDLC (Security Software Development Lifecycle) is a process used to develop software with built-in security measures. It involves integrating security practices at every stage of the software development life cycle, including planning, design, implementation, testing, and deployment. The goal is to ensure that security is considered and addressed throughout the entire development process, reducing vulnerabilities and improving the overall security of the software.
What is the difference between SDLC and SSDLC?
SDLC is the general software development process, while SSDLC is a security-focused approach within SDLC that emphasizes integrating security practices at every stage.
What are the 7 core phases of software development?
The seven core phases of secure software development lifecycle are: 1) Planning 2) Requirements 3) Design 4) Implementation 5) Verification 6) Maintenance 7) Incident response




